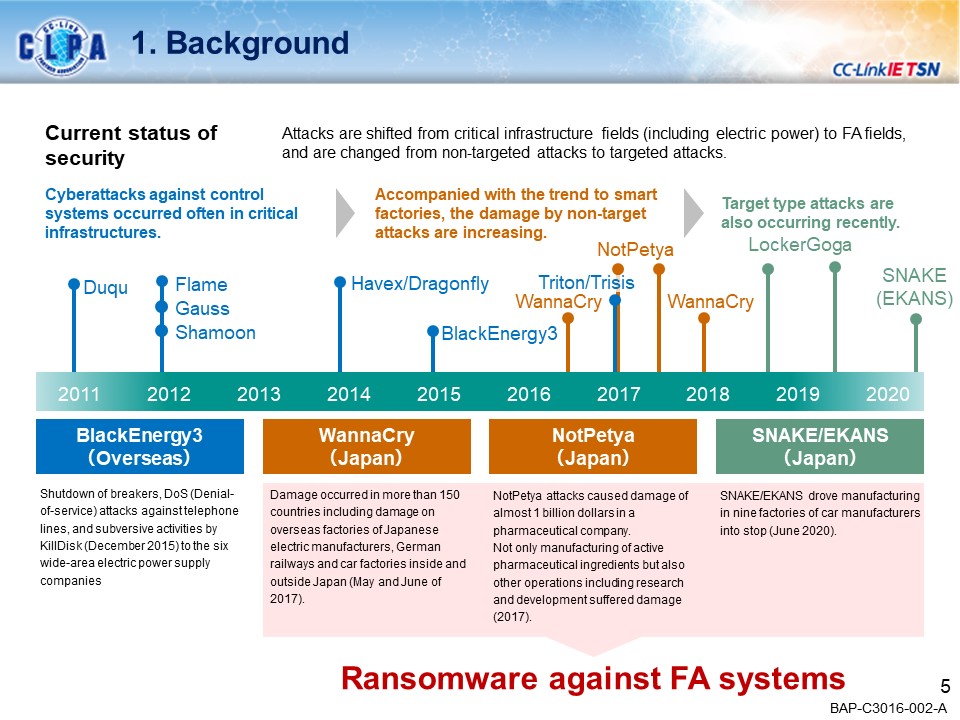
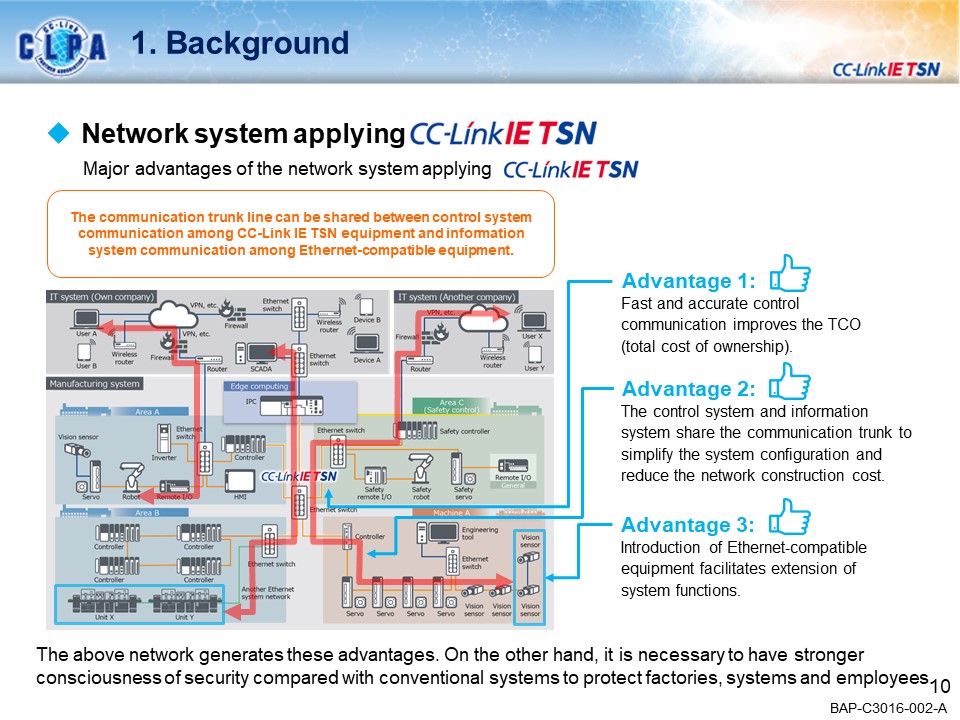
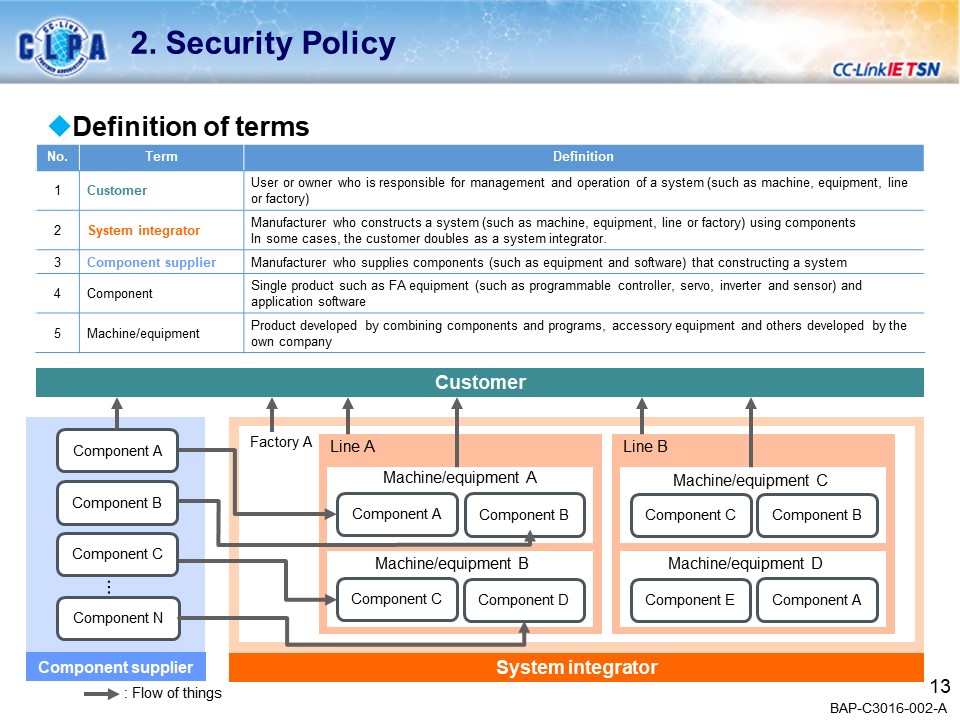
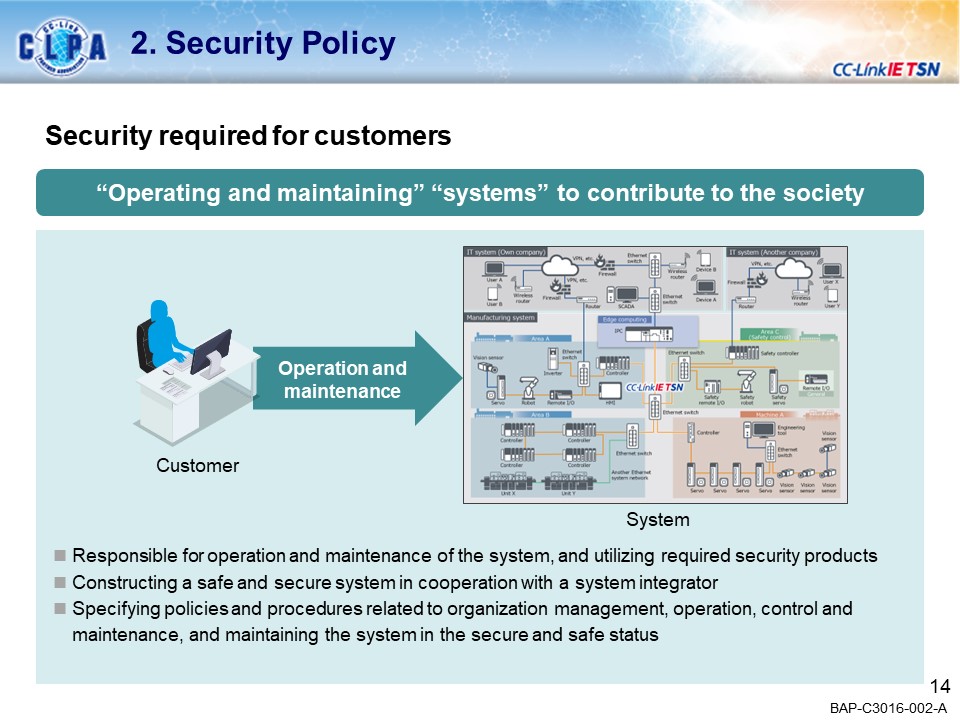
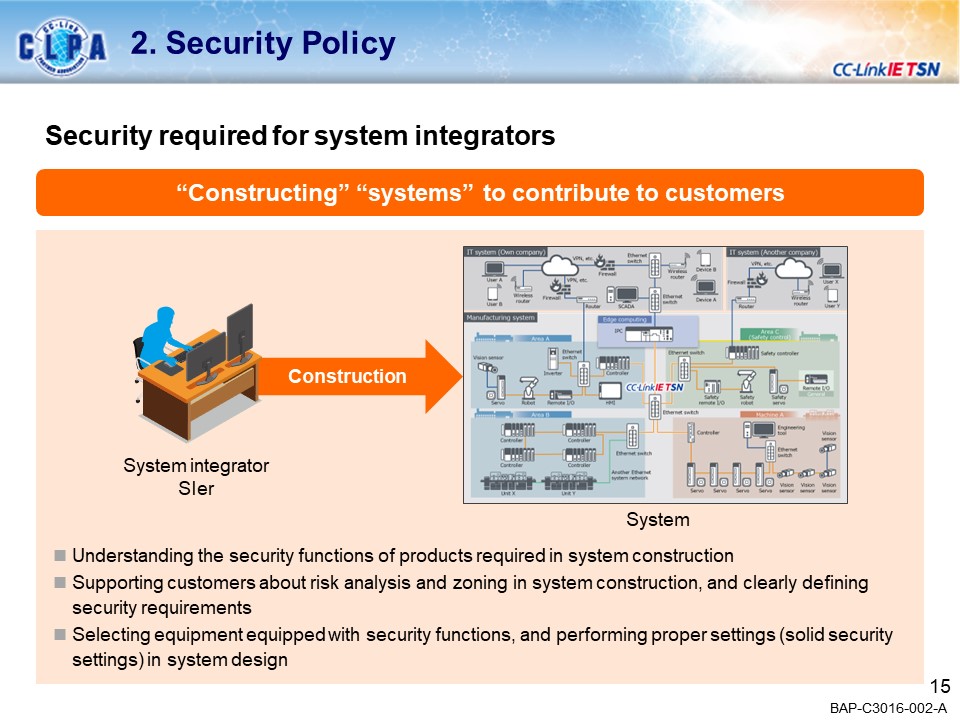
SecurityNEW!
A Secure World with CC-Link IE TSN

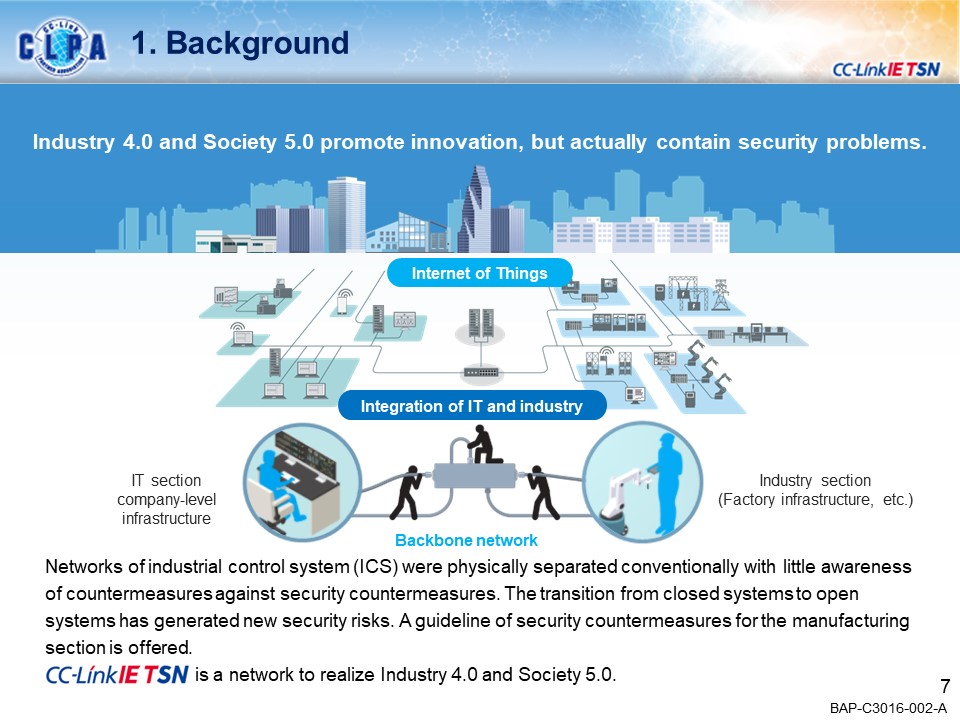
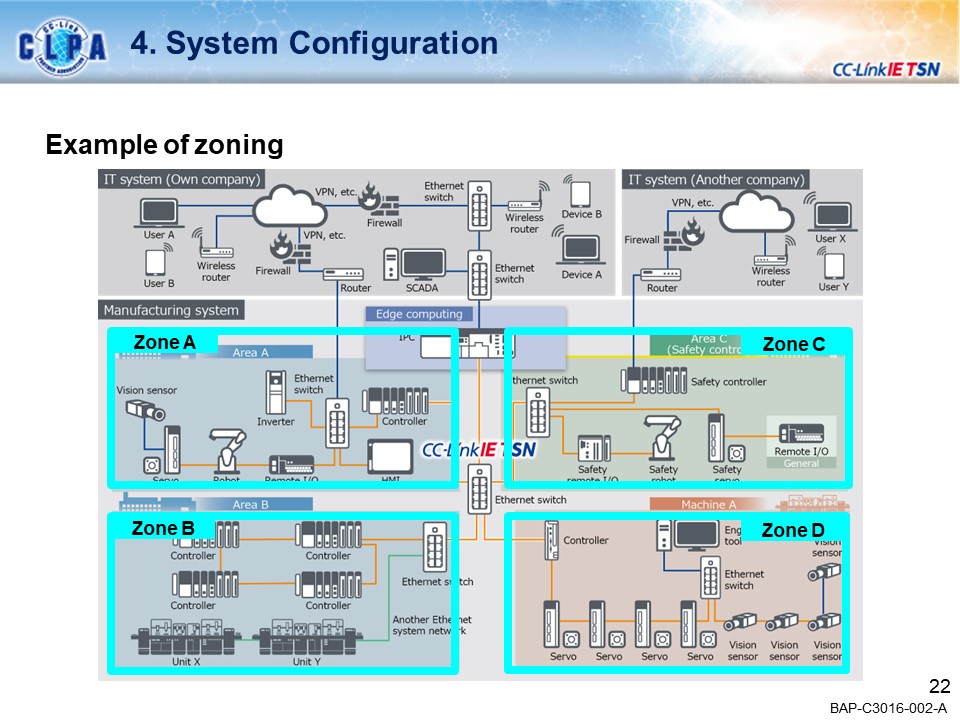
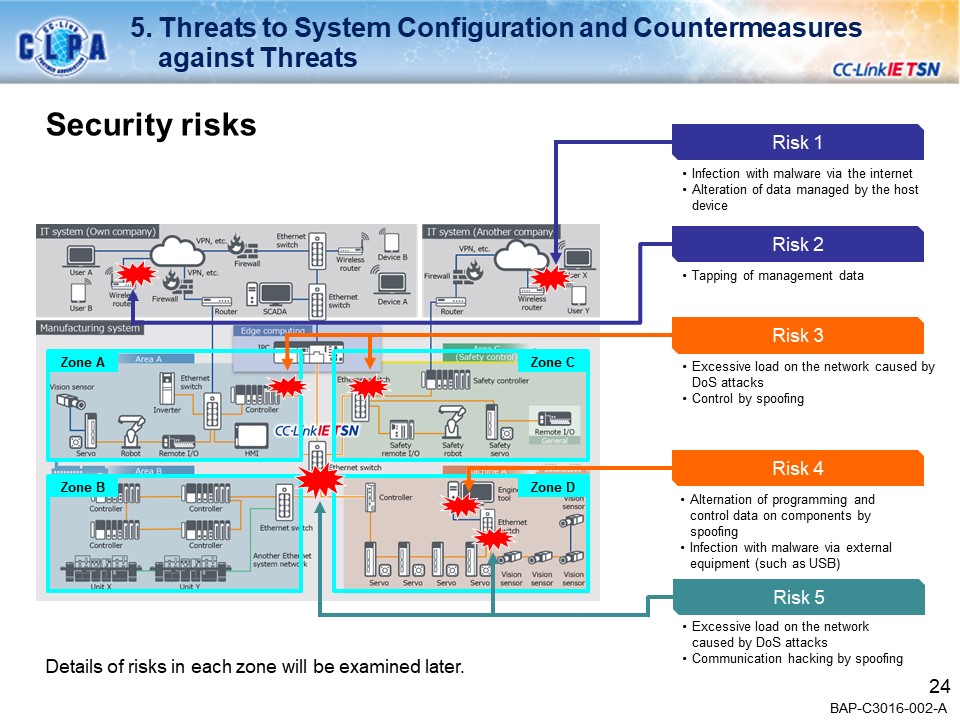
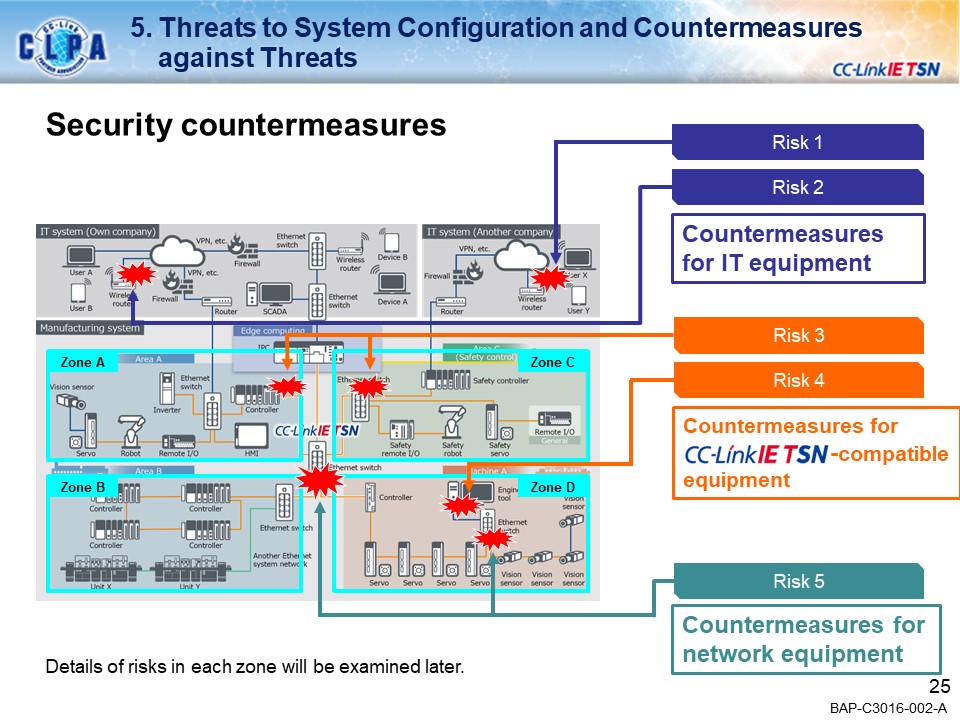
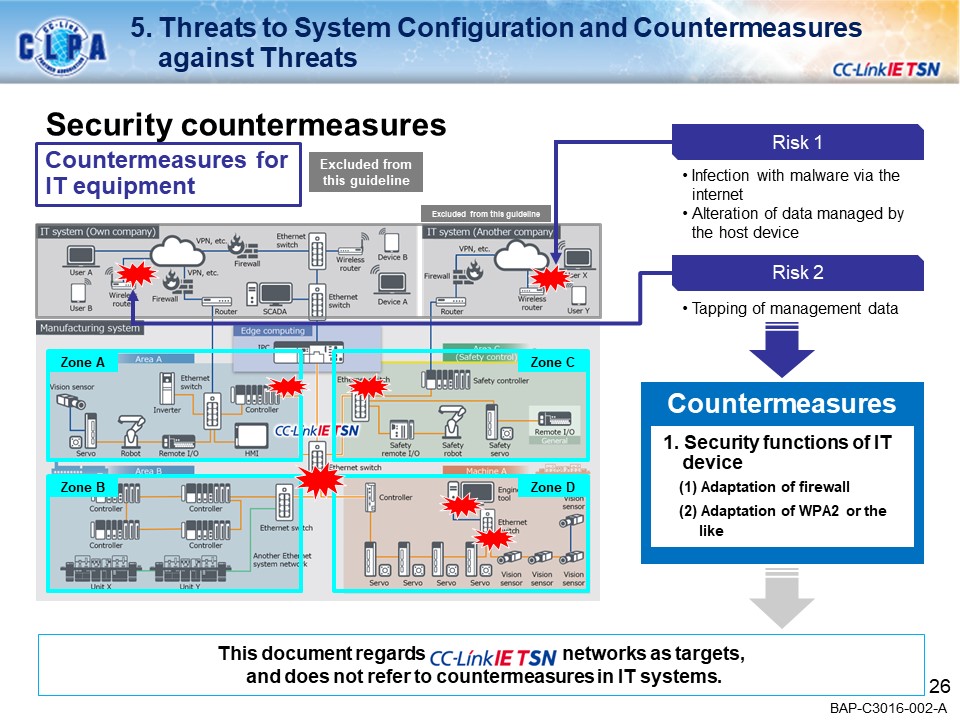
CC-Link IE TSN seamlessly links FA (Production Site: OT) and IT systems, enabling a wide variety of applications in the manufacturing industry.Our goal is to create a secure environment against the security threats that are coming to FA.
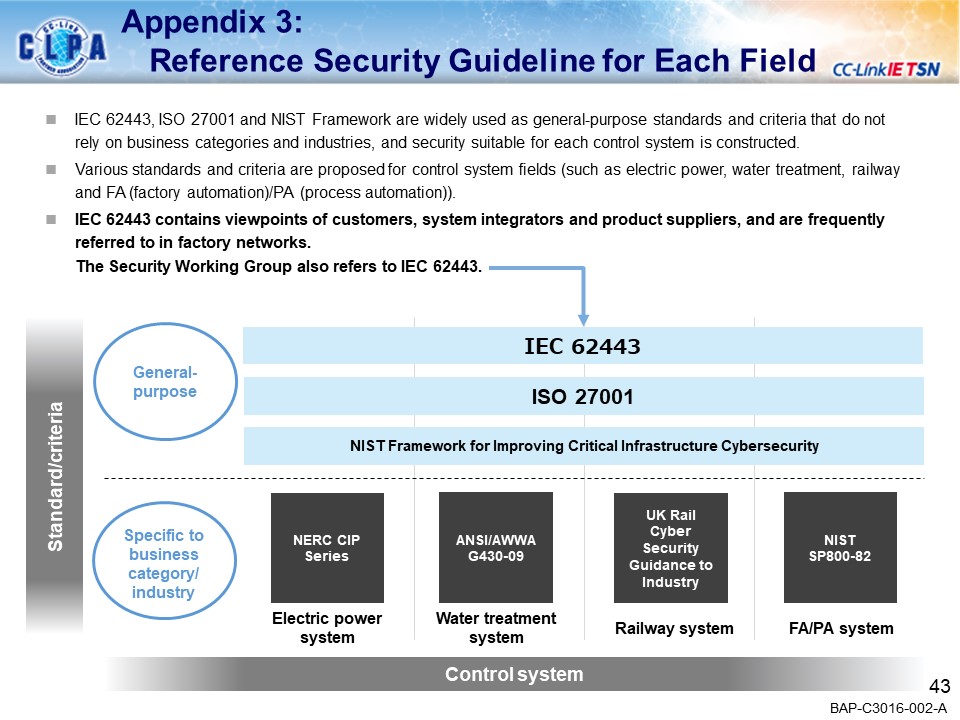
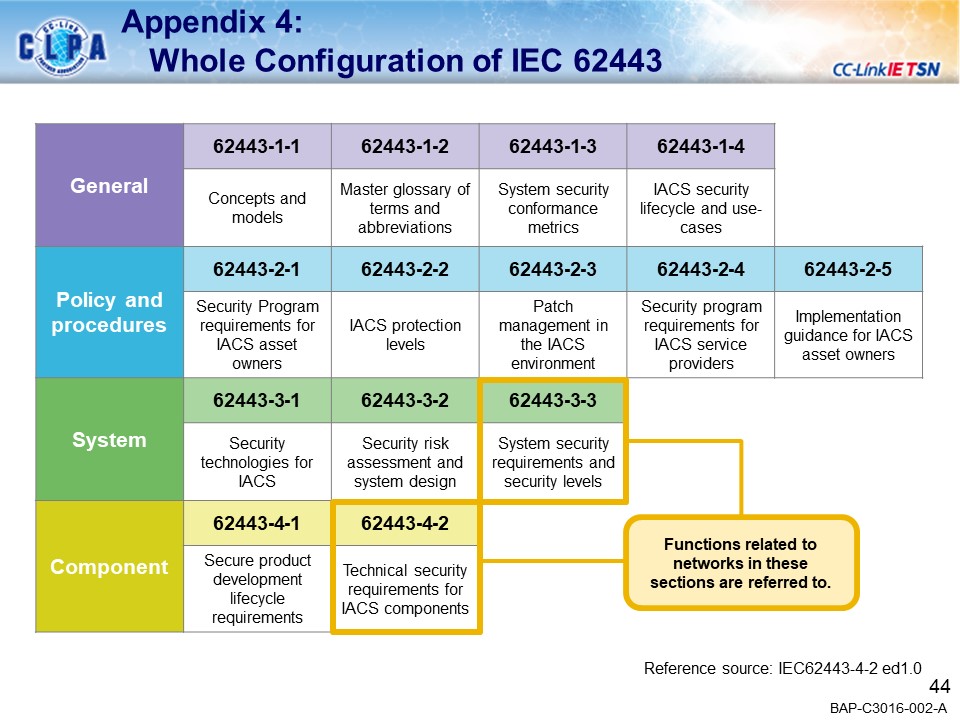
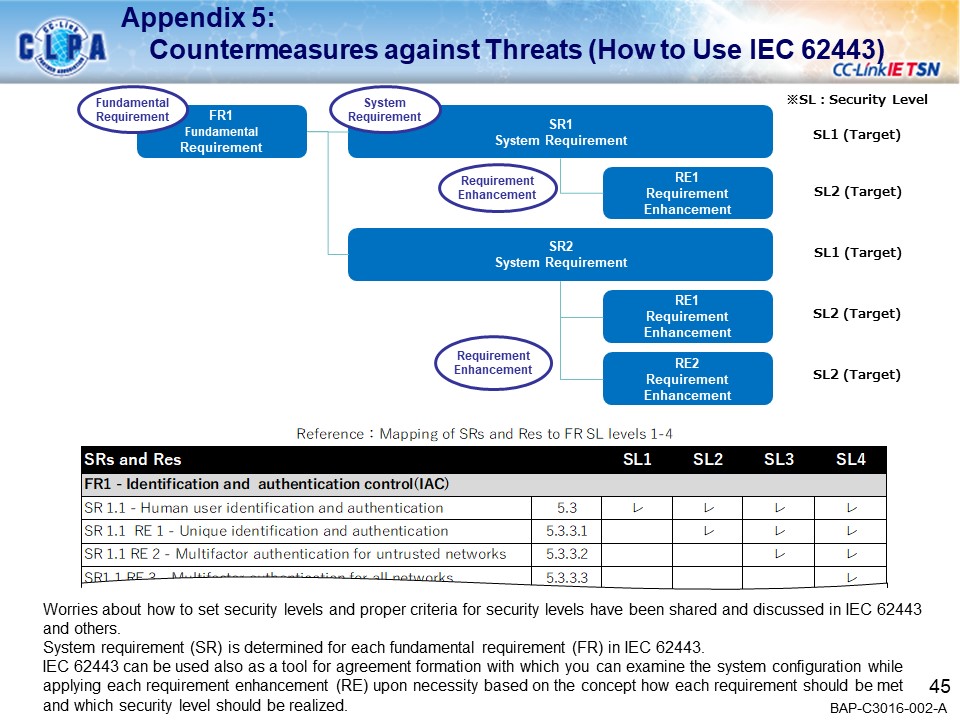
Security Guideline
- Introducing the concept of security for FA systems using CC-Link IE TSN.
A detailed version of the security guidelines is available on download page.
*Material downloads are for CLPA members only.
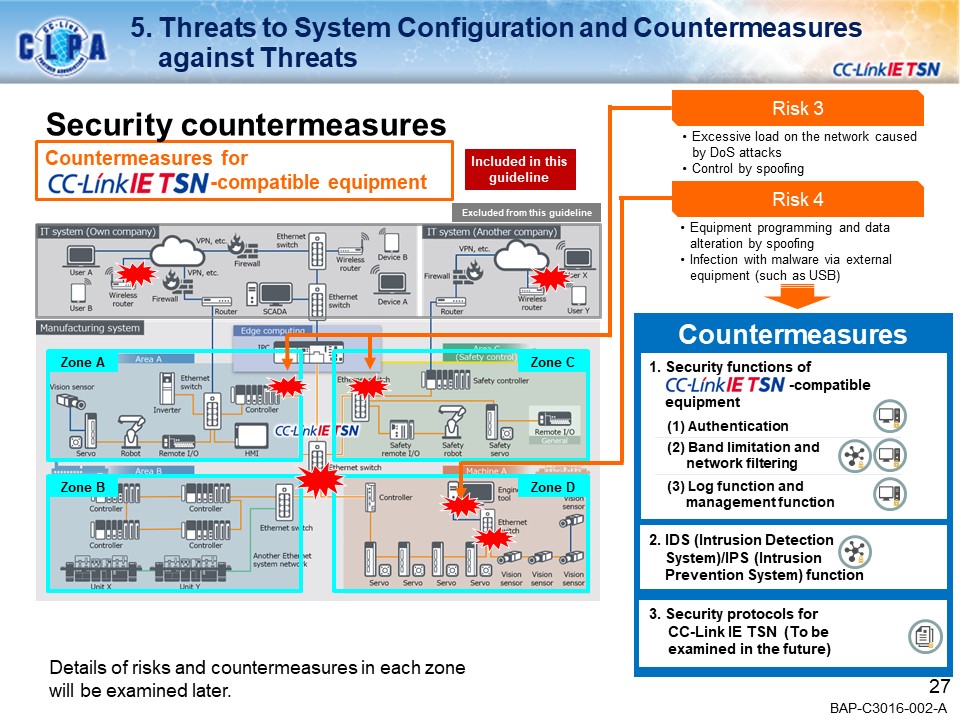
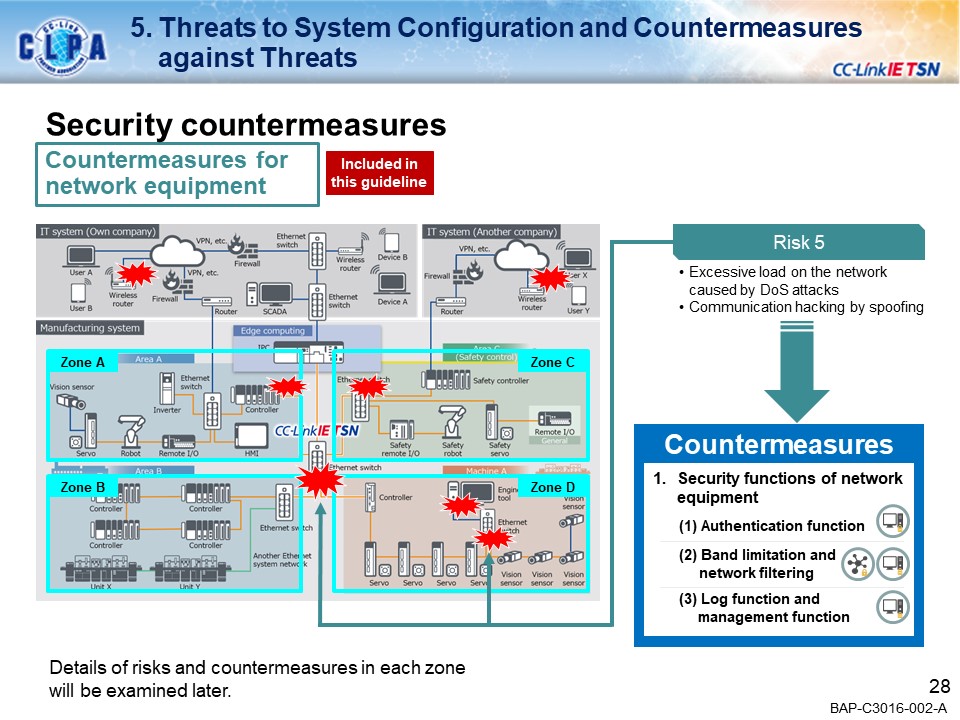
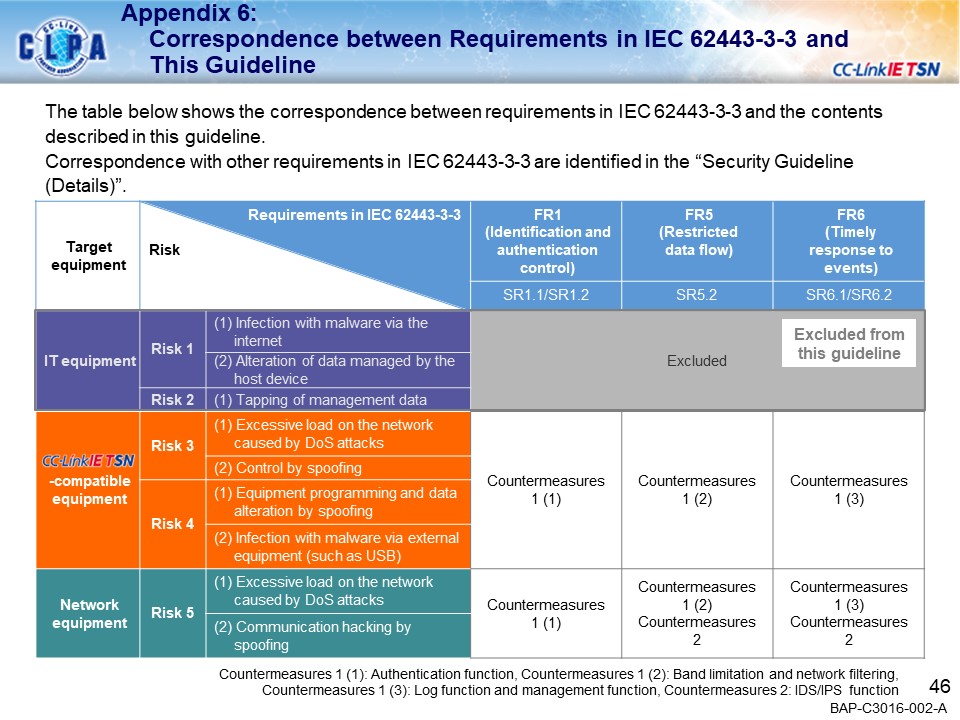
Examples of secure countermeasures against threats
- Introduction of specific threats and security Countermeasures in the CC-Link IE TSN network system
| Use cases | Countermeasures |
|---|---|
| Case 1: Ransomware infection via external device | IDS/IPS function |
| Case 2: DoS attacks | Band limitation and network filtering |
| Case 3: Tamper by spoofing | Authentication function |
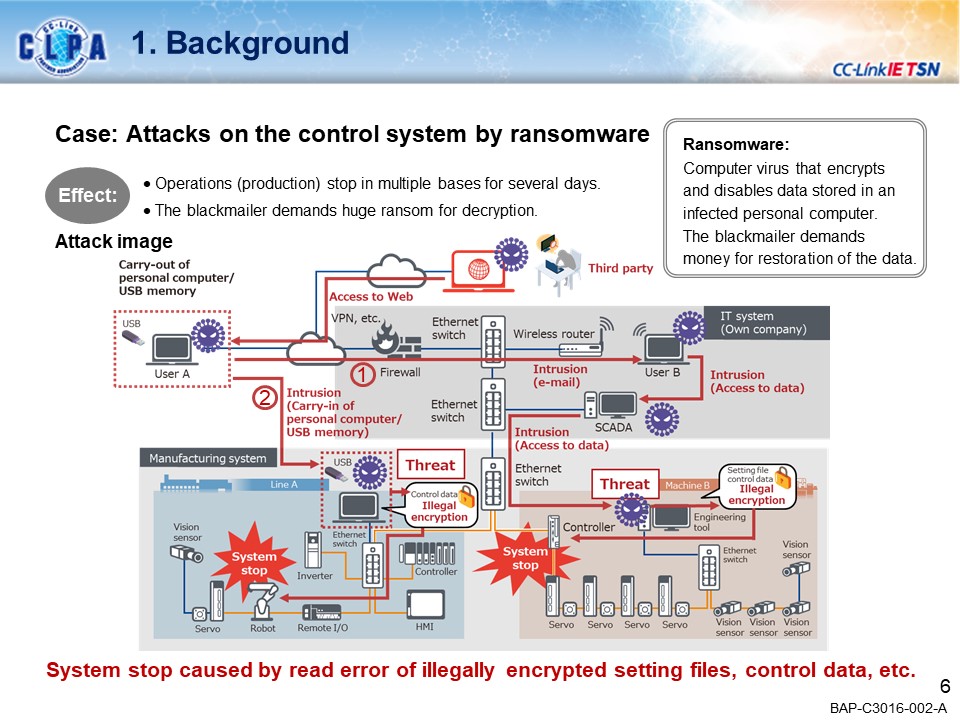
Ransomware infection
When the virus-carrying USB is connected to the computer, it will infect the computer, making the device data in the CC-Link IE TSN system unusable, and may ask for ransom on the grounds of restoring the data or not disclosing the data. The system may stop if the system cannot read the unauthorized encrypted configuration files or control data.


Examples of security countermeasuresIDS/IPS function
Detects or prevents the spread of viruses that cannot be addressed by network filtering, which prevents based on IP address or TCP/UDP port number.

DoS attacks
If a malicious third party sends a large amount of data to CC-Link IE TSN compatible products, the communication between products and line monitor will not work properly, and instructions from the administrator may not be transmitted to the device.
*DoS: Denial-of-service attacks


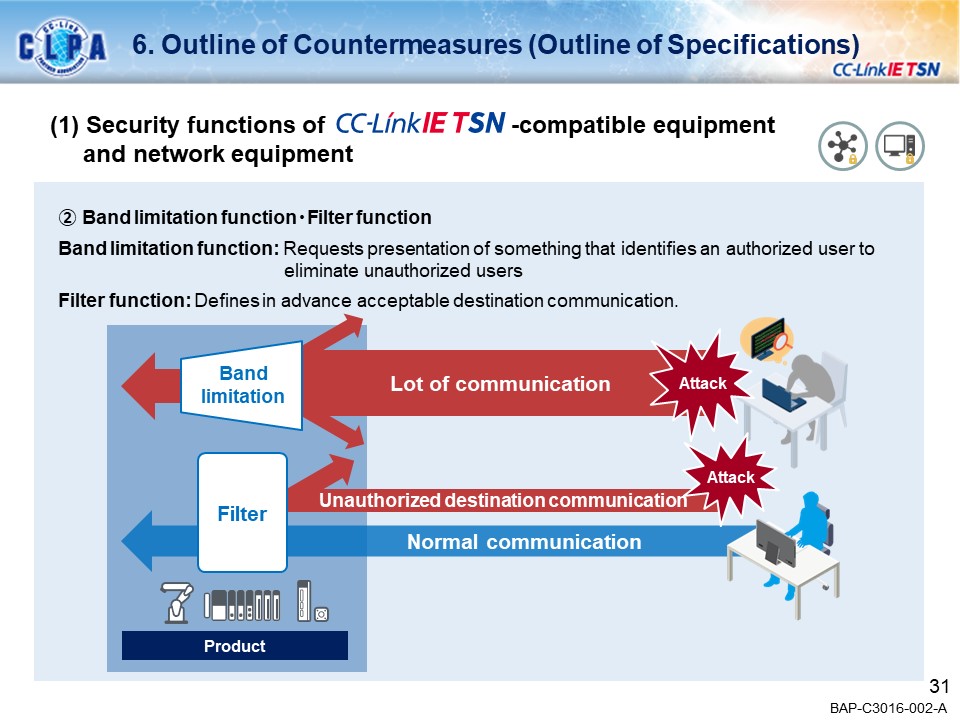
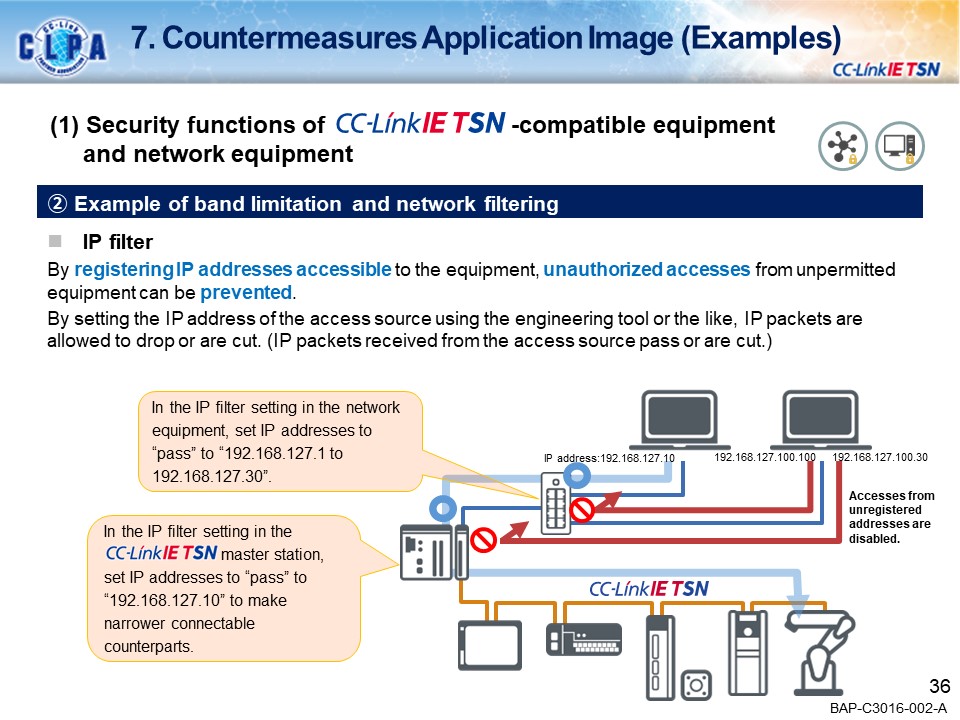
Examples of security countermeasuresBand limitation and network filtering
Registering IP addresses that can access the equipments prevents unauthorized access from non-authorized devices. By setting the IP address of the access source using an engineering tool, etc., IP packets can be transmitted or blocked. (Transmits or blocks IP packets received from the access source.)

Tamper by spoofing
If a third party pretends to be a legitimate user and illegally rewrites the program or setting data of CC-Link IE TSN compatible devices, the devices will operate improperly due to incorrect information.


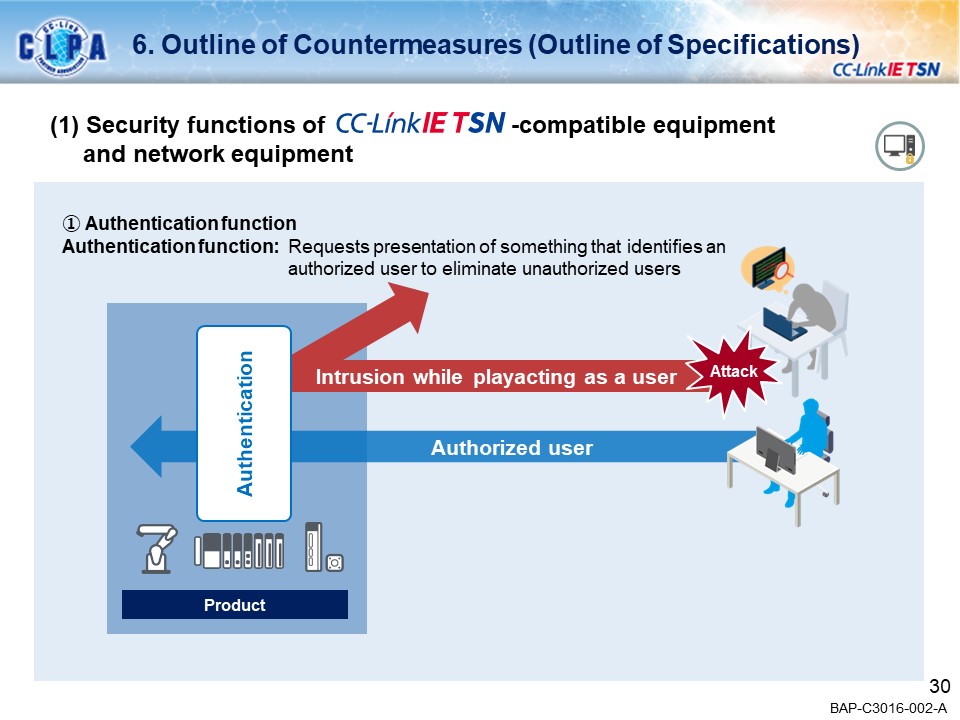
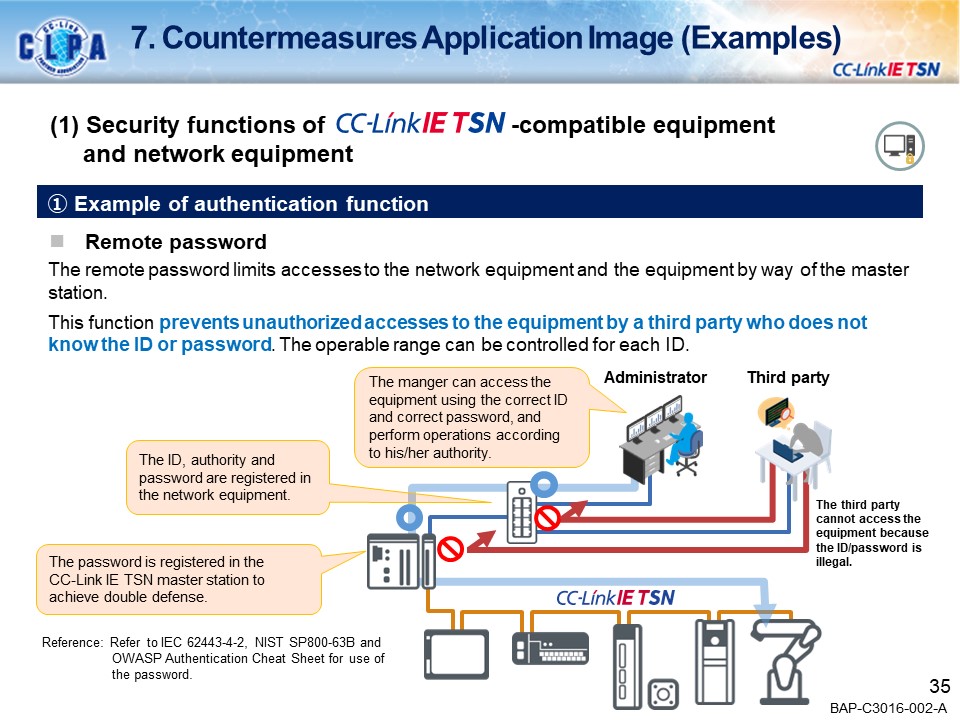
Examples of security countermeasuresAuthentication function
The remote password limits accesses to the network equipment and the equipment by way of the master station.
This function prevents unauthorized accesses to the equipment by a third party who does not know the ID or password. The operable range can be controlled for each ID.

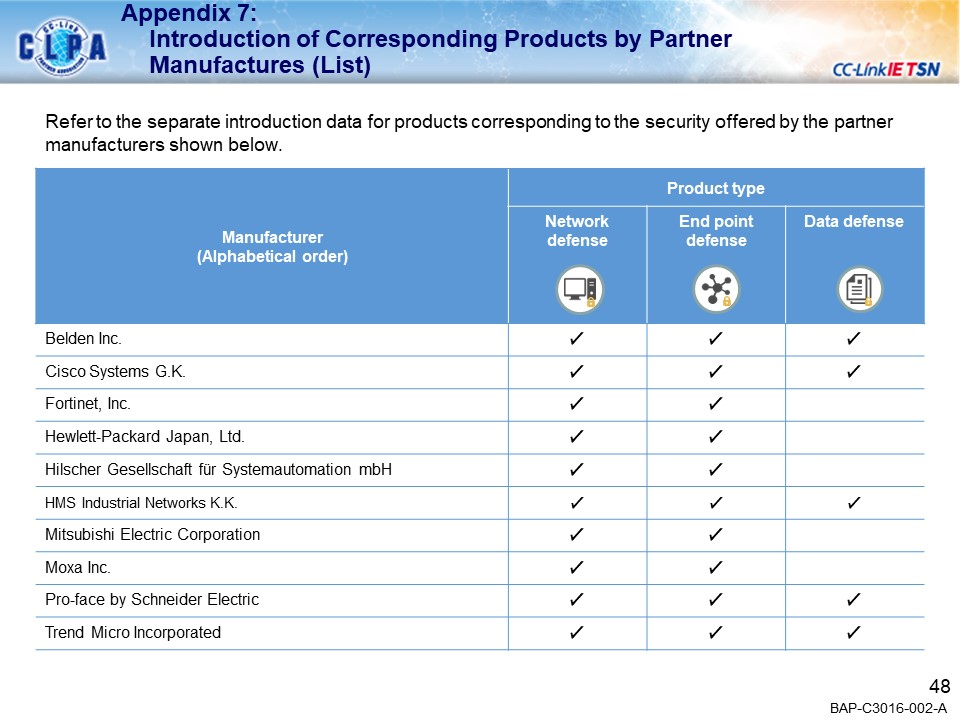
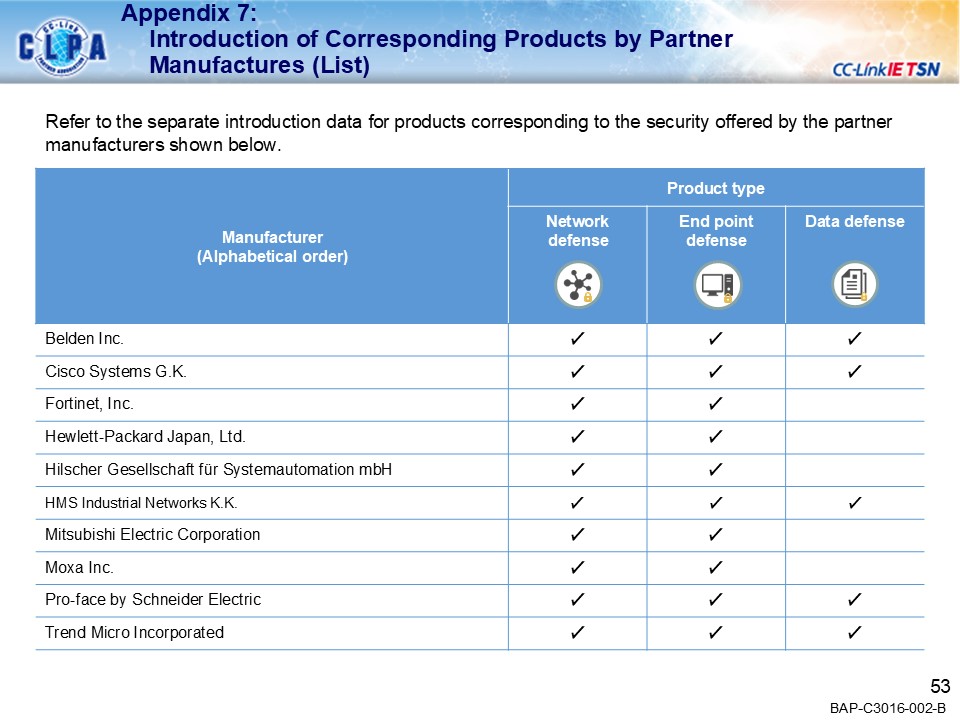
Security compatible products by CLPA partners
- The following is the introduction of security compatible products from partner manufacturers. For details on security features, please contact each partner manufacturer.